When configuring network services on any Linux machine, managing open ports and firewall rules is crucial for both security and functionality. Here’s a detailed guide explaining all essential commands, walking you through common tools and steps to manage ports and firewalls on Ubuntu and CentOS systems.
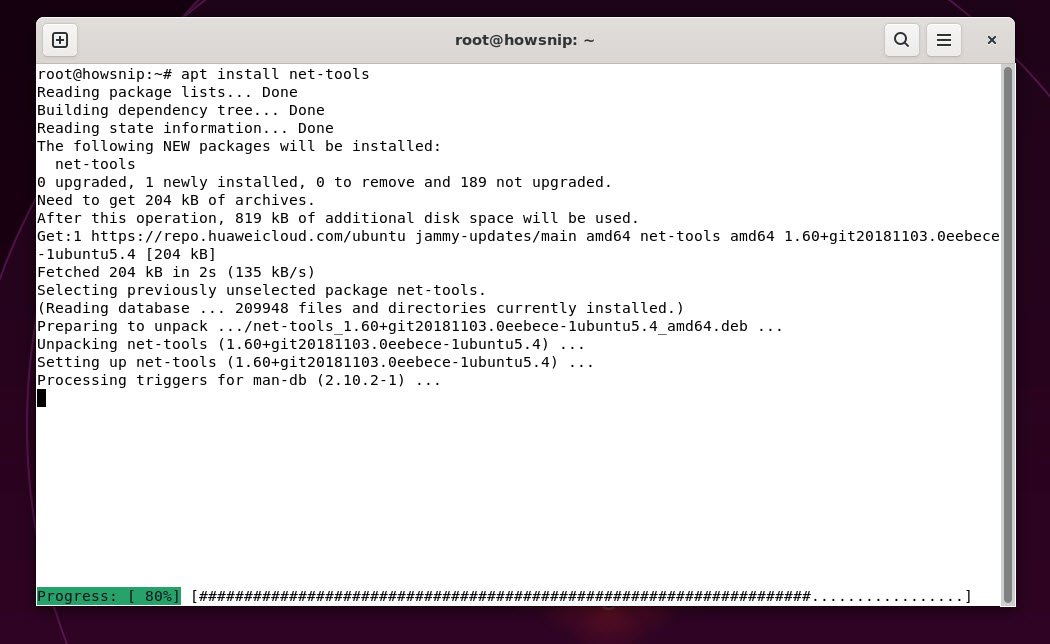
Start by installing the net-tools package, as it includes helpful networking utilities such as netstat, which is essential for port monitoring.
To install the package on Ubuntu, the command is:
Command: apt install net-toolsThis command uses the APT package manager to fetch and install the net-tools suite.
There are two primary commands to list open ports and currently listening services:
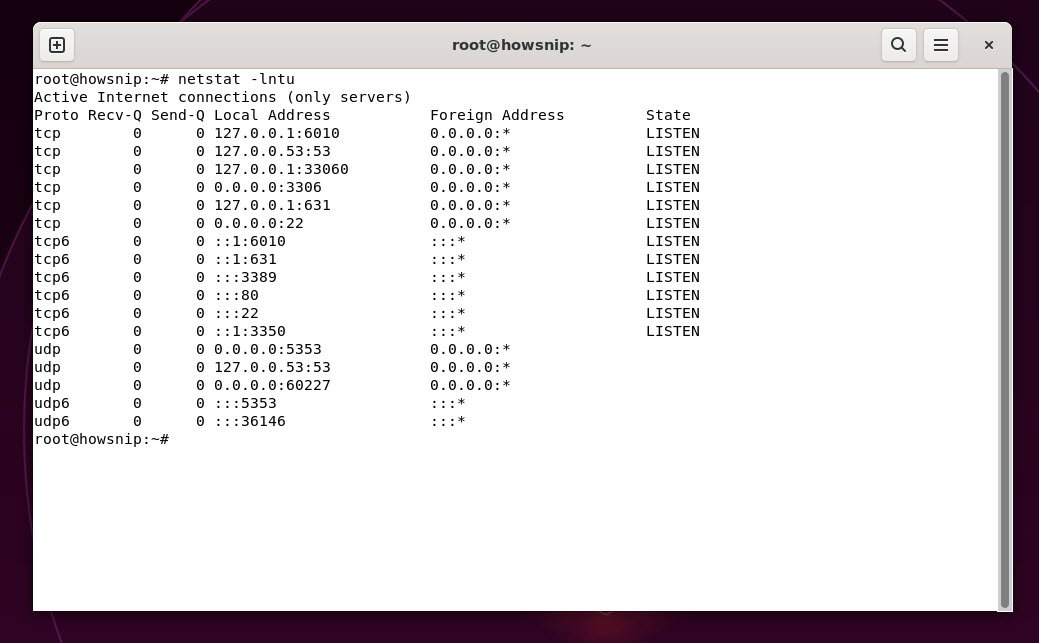
[#1]. Using Netstat
This command gives a detailed overview of services waiting for connections.
Command: netstat -lntuHere,
-l lists listening ports,
-n shows numerical addresses instead of resolving hostnames,
-t is for TCP, and
-u is for UDP.
[#2]. Using ss
The ss command is a faster, more modern alternative to netstat. This gives more or less the same open ports as netstat.
Command: ss -lntu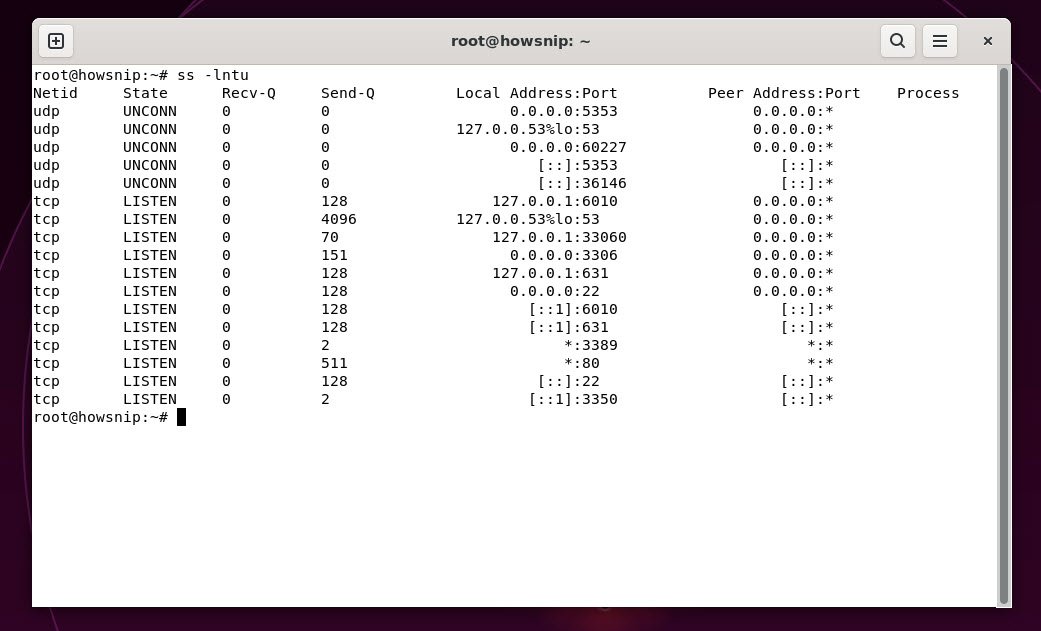
Checking If a Specific Port Is in Use
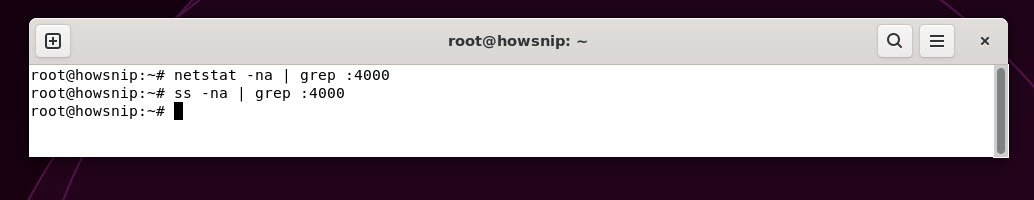
Before opening a new port (like 4000), it’s best practice to check if it’s already being used:
Using netstat/ss to check:
Command: netstat -na | grep :4000
Command: ss -na | grep :4000This searches for open connections or listeners on port 4000 using netstat/ss.
Allowing Traffic Through Ports
Depending on your Linux distribution and firewall system, use the following commands to allow network traffic through a desired port.
a) For opening a port in Ubuntu:
This command lets traffic through port 4000, using UFW (Uncomplicated Firewall), the default on Ubuntu.
Command: ufw allow 4000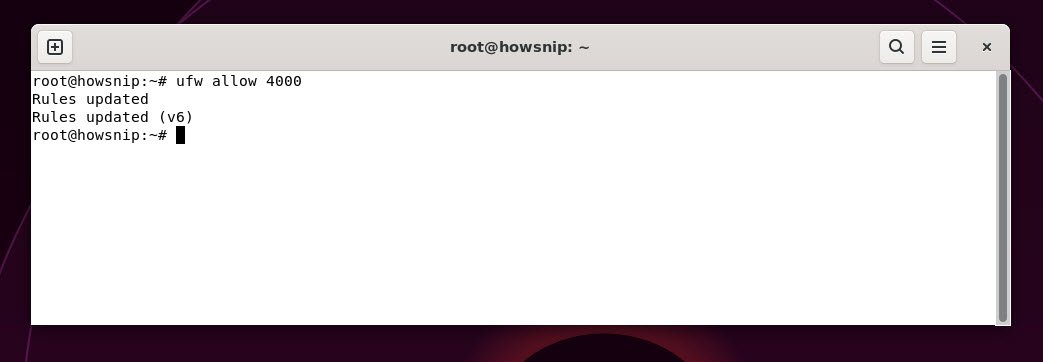
b) For CENTOS:
This command opens TCP port 4000 in real-time.
Command: firewall-cmd --add-port=4000/tcpc) For opening a port using IPTABLES:
This appends a rule to the INPUT chain, allowing TCP traffic to port 5000. Change port number and protocol as required.
Command: sudo iptables -A INPUT -p tcp --dport 5000 -j ACCEPT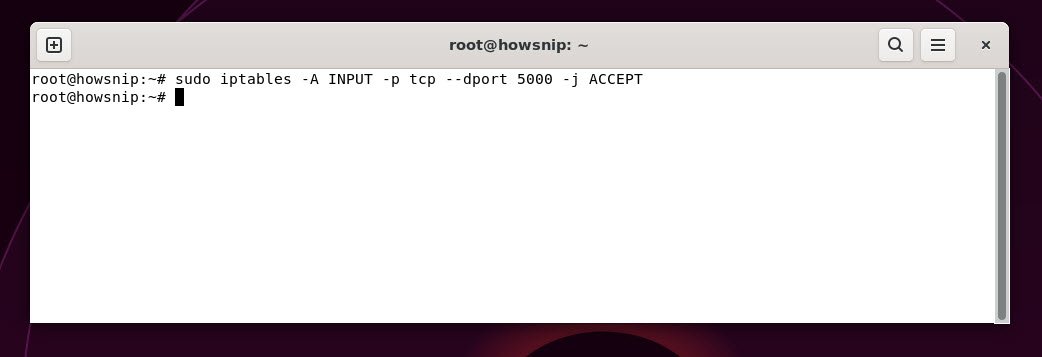
Testing Port Availability and Connectivity
After opening a port, it’s wise to test its availability and connectivity.
a) Listening with netcat:
The below command starts a netcat listener on port 4000. The ls | portion sends the output of ls to any client connecting to the port.
Command: ls | nc -l -p 4000b) Connecting with telnet:
Use telnet from another host to attempt a connection to port 4000. Replace the IP address with your server’s public or private address.
Command: telnet 10.228.1.75 4000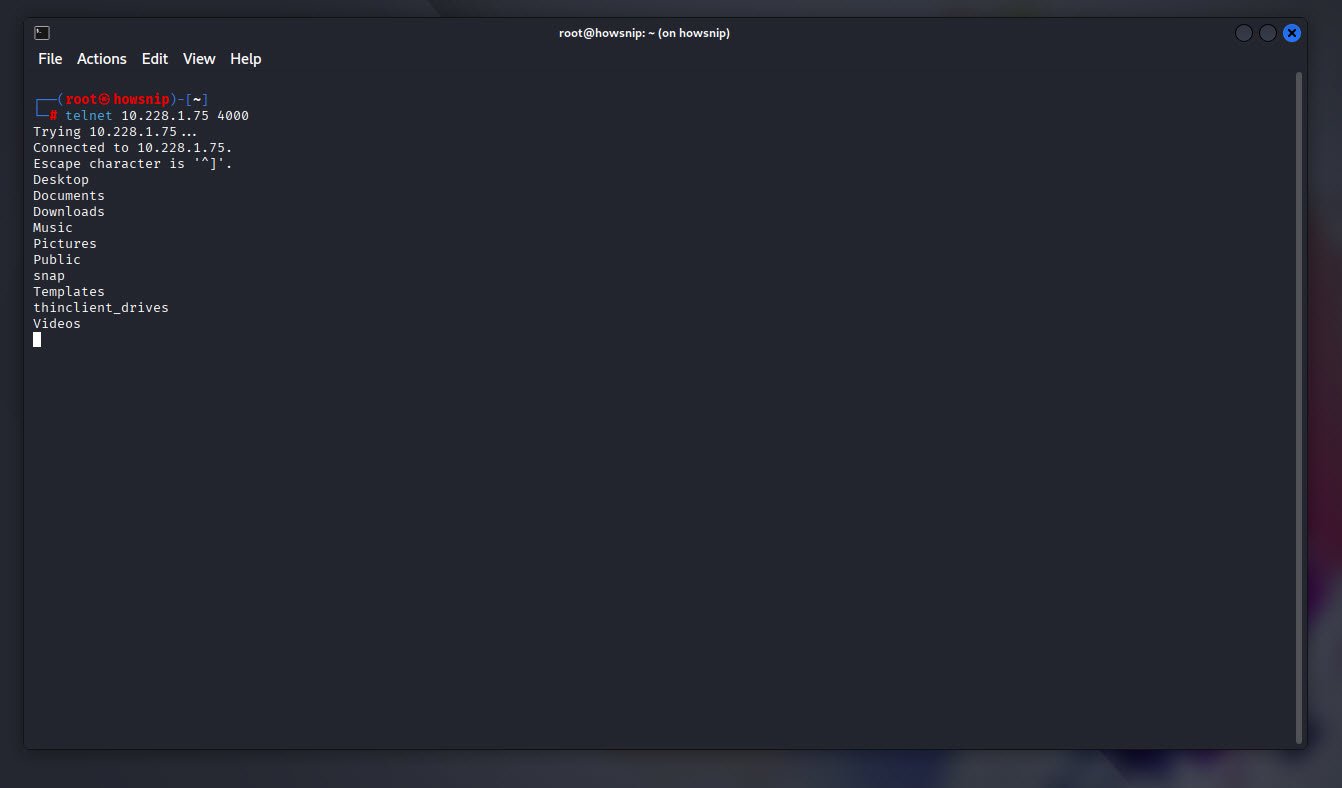
c) Scanning with nmap:
The below command checks whether port 4000 is open on the specified host using the nmap scanner.
Command: nmap 10.228.1.75 -p 4000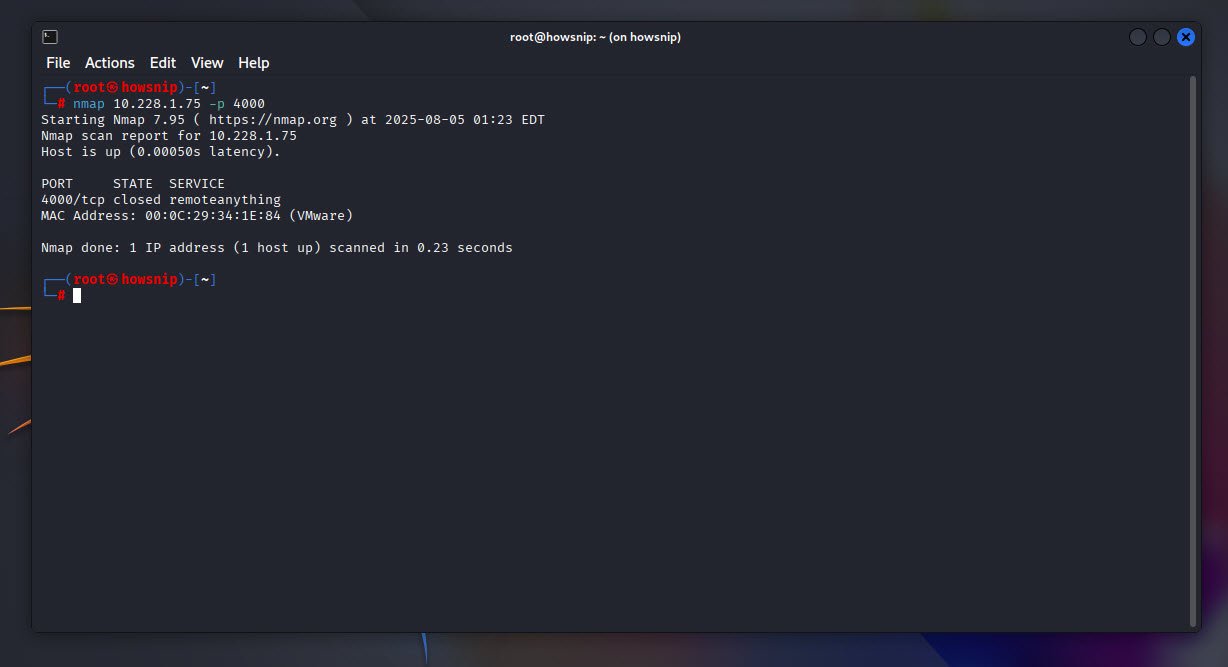
d) Scanning a range of ports with netcat:
This command scans ports 1 through 1,024 to find open ports on the server.
Command: nc -z -v -n 10.228.1.75 1-1024The -z flag runs netcat in scanning mode, -v makes it verbose, and -n skips DNS resolution.
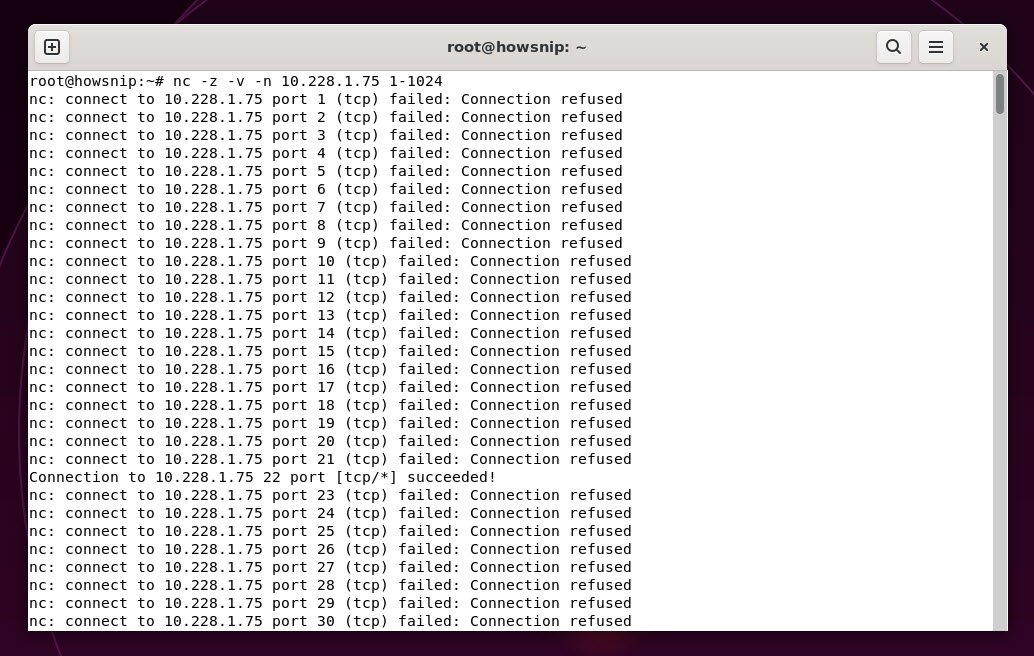
Verifying Firewall Rules
After configuring the firewall, it’s best to inspect the current rules to ensure configurations took effect:
a) For iptables:
This lists all active rules in the filter table, showing which ports and IPs are allowed or blocked.
Command: iptables -L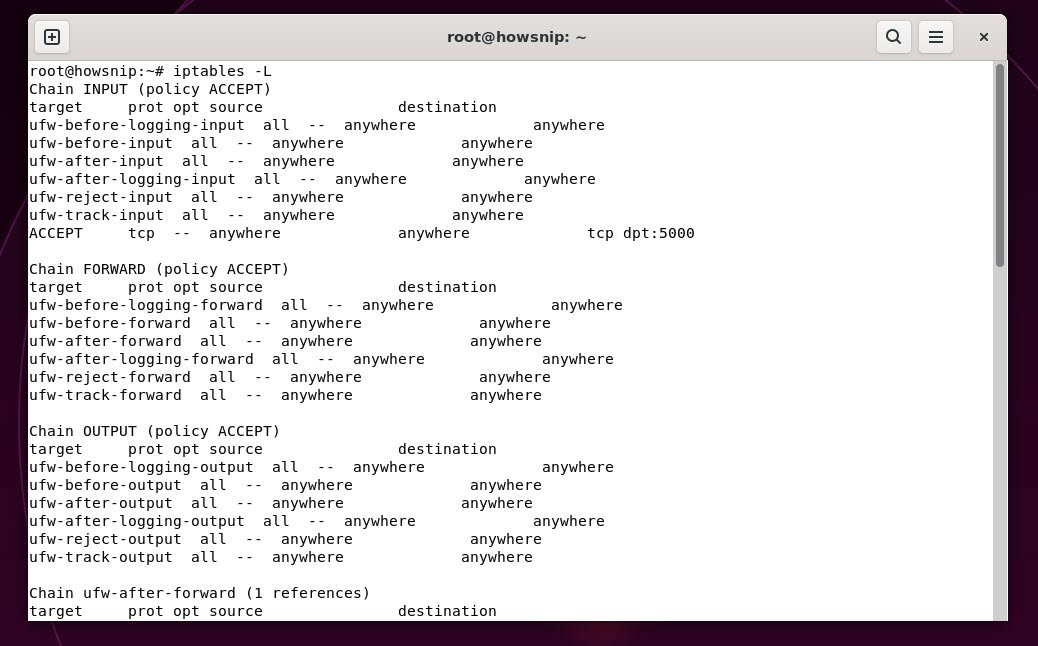
b) For ufw:
This command displays the current status of UFW and details any permitted or denied ports.
Command: ufw status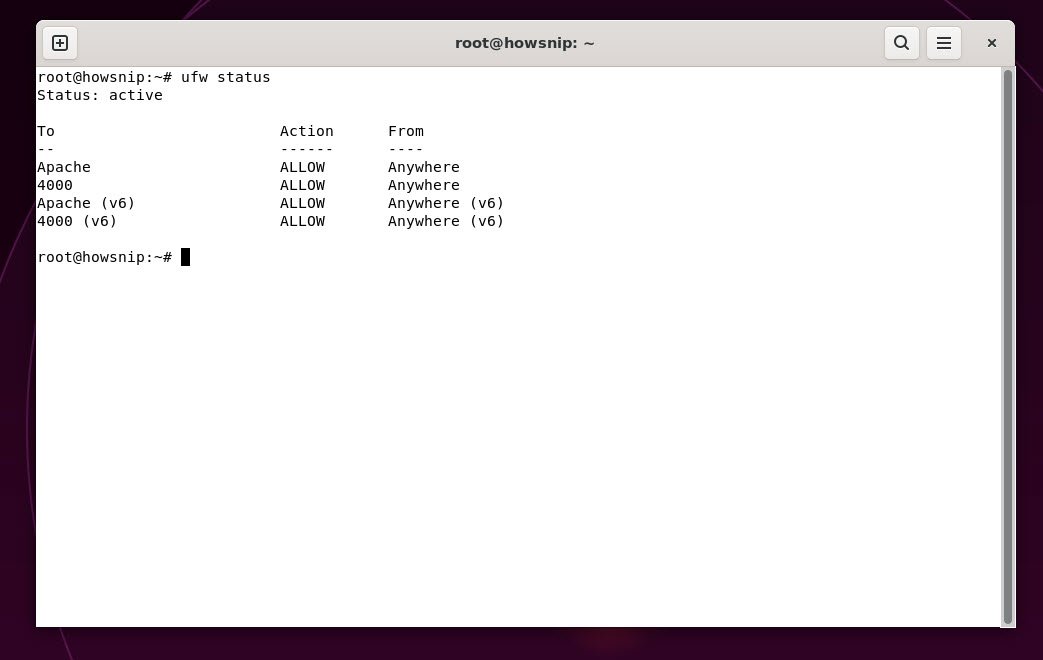
c) For firewalld:
This command shows all active firewall settings, including zones, allowed services, and open ports.
Command: firewall-cmd --list-allAll above commands form the backbone of network and port management for any Linux server. Always check ports before opening them to avoid conflicts, test connectivity after making changes, and confirm your firewall rules for system security.
This approach ensures both service availability and network safety on Ubuntu, CentOS, and other Linux distributions.


